 Yet another red flag on security of the Internet of Things (IoT) has been raised, this time by none other than the reputed company, Hewlett-Packard (HP).
Yet another red flag on security of the Internet of Things (IoT) has been raised, this time by none other than the reputed company, Hewlett-Packard (HP).
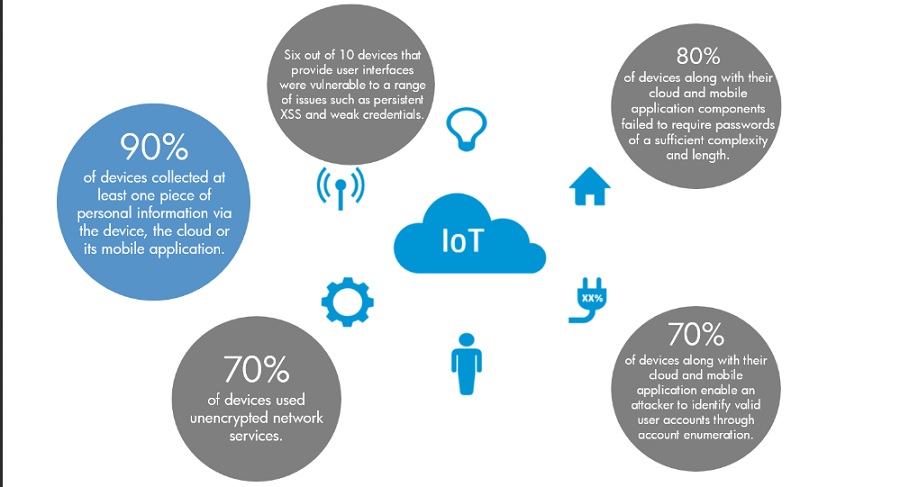
An HP Security Research team reviewed 10 of the most popular devices in some of the most common IoT niches, only to find an alarmingly high average number of vulnerabilities per device. Vulnerabilities ranged from Heartbleed to Denial of Service to weak passwords to cross- site scripting. Clearly, the day is not far off when we will see hackers invading people’s privacy or walking away with the personal data from devices connected to the IoT such as televisions and smoke detectors.
 Here are excerpts from the HP Research team’s report:
Here are excerpts from the HP Research team’s report:
Privacy Concerns
With many devices collecting some form of personal information such as name, address, data of birth, health information and even credit card numbers, those concerns are multiplied when you add in Cloud services and mobile applications that work alongside the device. And with many devices transmitting this information unencrypted on your home network, users are one network misconfiguration away from exposing this data to the world via wireless networks. Cloud services, which we discovered most of these devices use, are also a privacy concern as many companies race to take advantage of the cloud and services it can provide from the internet. Do these devices really need to collect this personal information to function properly?
Insufficient Authentication/Authorization
An attacker can use vulnerabilities such as weak passwords, insecure password recovery mechanisms, poorly protected credentials, etc. to gain access to a device. A majority of devices along with their cloud and mobile components failed to require passwords of sufficient complexity and length with most allowing passwords such as 1234.
Lack of Transport Encryption
Transport encryption is crucial given that many of these devices are collecting and transmitting data that can be considered sensitive in nature. We found that a majority of the devices failed to encrypt network services transmitting data via the internet and the local network. The importance of transport encryption rises significantly when you consider that data is being passed between the device and the cloud and a mobile application.
Insecure Web Interface
Six of the 10 devices we tested displayed concerns with their web interface. These concerns were issues such as persistent cross – site scripting, poor session management and weak default credentials.
We identified a majority of devices along with their cloud and mobile counterparts that enable an attacker to determine valid user accounts using mechanisms such as the password reset features. These issues are of particular concern for devices that offer access to devices and data via a Cloud website.
Insecure Software/Firmware
Given that software is what makes these devices function, it was rather alarming that 60% of devices displayed issues including no encryption during downloading of the update along with the update files themselves not being protected in some manner. In fact some downloads we re-intercepted, extracted and mounted as a file system in Linux where the software could be viewed or modified.
In conclusion, the research team has recommended the following steps:
- Conduct a security review of your device and all associated components
- Implement security standards that all devices must meet before production
- Ensure security is a consideration throughout the product lifecycle
Image Credit: HP Research
– Advertising Message –
